I'm currently experimenting with migrating an existing Apache + PHP-FPM setup to LSWS, and ran into an issue involving External App definitions. This is using LSWS 6.0.8.
For storage latency reasons, we prefer to have our PHP processes always running, to ensure that opcaches are maximally kept alive and thus minimize the need to hit the disk (even at the cost of consuming more memory). For that reason, we currently have a bunch of separate always-on PHP-FPM processes, one per user, with each vhost configured to talk to its own instance over a UNIX socket.
To run this under LSWS, ProcessGroup mode seems pretty close, but there doesn't seem to be a way to get around the finite lifetime of the lsphp processes it spawns. Instead, I found this article titled "Set up LSPHP in Command Line Mode" that describes how to run LSPHP as separate instances, and then how to get LSWS to talk to them as External Apps.
That works great and matches our existing setup closely, but there's one problem: using a server-level External App definition as described in that article, I can't get individual vhosts (as parsed from their Apache configs) to talk to individual UNIX sockets. I would've expected that using a $VH_NAME or $VH_USER variable in the External App's address line would've worked for this, but it turns out these variables are empty at runtime.
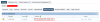
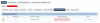
Trying to run a PHP script under such a vhost discovered through Apache config results in a 503 with this in the error.log:
Which indeed shows that the variable is not getting filled in.
I figured this might have something to do with the fact that the Handler Name field in the Script Handler section mentions "Server Level". Indeed, if I replace the Apache-loaded configs with LSWS-native vhosts (i.e. disable loading of Apache configs and configure the vhosts in XML instead), and then add the same External App and Script Handler at the Virtual Host level, then the variable does get substituted and everything works ok.
That kind of makes sense, since at the server-level there is no individual user/vhost name to speak of yet, but I would've expected the definition to get inherited by vhosts and have its variables substituted only there.
Is there a way to get vhosts loaded from Apache to use vhost-level External App definitions like this, in which $VH_USER and $VH_NAME would work? Or some other method of pointing each one to a vhost-specific UNIX socket for external LSPHP processes? For ProcessGroup mode there are some LSWS-specific Apache directives listed, but I couldn't find any for defining external apps this way.
For storage latency reasons, we prefer to have our PHP processes always running, to ensure that opcaches are maximally kept alive and thus minimize the need to hit the disk (even at the cost of consuming more memory). For that reason, we currently have a bunch of separate always-on PHP-FPM processes, one per user, with each vhost configured to talk to its own instance over a UNIX socket.
To run this under LSWS, ProcessGroup mode seems pretty close, but there doesn't seem to be a way to get around the finite lifetime of the lsphp processes it spawns. Instead, I found this article titled "Set up LSPHP in Command Line Mode" that describes how to run LSPHP as separate instances, and then how to get LSWS to talk to them as External Apps.
That works great and matches our existing setup closely, but there's one problem: using a server-level External App definition as described in that article, I can't get individual vhosts (as parsed from their Apache configs) to talk to individual UNIX sockets. I would've expected that using a $VH_NAME or $VH_USER variable in the External App's address line would've worked for this, but it turns out these variables are empty at runtime.


Trying to run a PHP script under such a vhost discovered through Apache config results in a 503 with this in the error.log:
Code:
2022-08-16 14:21:32.398793 [INFO] [1313881] [T0] [192.168.56.1:44716:HTTP2-15#_AdminVHost] add child process pid: 1313896, procinfo: 0x28ee480
2022-08-16 14:21:37.215833 [INFO] [1313881] [T0] [192.168.56.1:51406-1#APVH_acc1.be:81] connection to [uds://tmp/lsphp-.sock] on request #0, confirmed, 0, associated process: 0, running: 0, error: No such file or directory!
2022-08-16 14:21:37.215838 [INFO] [1313881] [T0] [uds://tmp/lsphp-.sock] Connection refused, restart!
2022-08-16 14:21:37.215852 [INFO] [1313881] [T0] [192.168.56.1:51406-1#APVH_acc1.be:81] connection to [uds://tmp/lsphp-.sock] on request #0, confirmed, 0, associated process: 0, running: 0, error: No such file or directory!
2022-08-16 14:21:37.215853 [INFO] [1313881] [T0] [uds://tmp/lsphp-.sock] Connection refused, restart!
2022-08-16 14:21:37.215860 [INFO] [1313881] [T0] [192.168.56.1:51406-1#APVH_acc1.be:81] connection to [uds://tmp/lsphp-.sock] on request #0, confirmed, 0, associated process: 0, running: 0, error: No such file or directory!
2022-08-16 14:21:37.215861 [INFO] [1313881] [T0] [uds://tmp/lsphp-.sock] Connection refused, restart!
2022-08-16 14:21:37.215862 [NOTICE] [1313881] [T0] [192.168.56.1:51406-1#APVH_acc1.be:81] Max retries has been reached, 503!
2022-08-16 14:21:37.215872 [NOTICE] [1313881] [T0] [192.168.56.1:51406-1#APVH_acc1.be:81] oops! 503 Service UnavailableI figured this might have something to do with the fact that the Handler Name field in the Script Handler section mentions "Server Level". Indeed, if I replace the Apache-loaded configs with LSWS-native vhosts (i.e. disable loading of Apache configs and configure the vhosts in XML instead), and then add the same External App and Script Handler at the Virtual Host level, then the variable does get substituted and everything works ok.
That kind of makes sense, since at the server-level there is no individual user/vhost name to speak of yet, but I would've expected the definition to get inherited by vhosts and have its variables substituted only there.
Is there a way to get vhosts loaded from Apache to use vhost-level External App definitions like this, in which $VH_USER and $VH_NAME would work? Or some other method of pointing each one to a vhost-specific UNIX socket for external LSPHP processes? For ProcessGroup mode there are some LSWS-specific Apache directives listed, but I couldn't find any for defining external apps this way.
Last edited:
