Table of Contents
HTTP Strict Transport Security in LSWS
HTTP Strict Transport Security (HSTS) informs all user agents that they should only communicate with the web server using HTTPS. This can be used to prevent some attacks that downgrade connections from HTTPS to HTTP.
This wiki will cover setting up HSTS with LiteSpeed Web Server (LSWS), both for LSWS installations using Apache configuration files and those using LSWS-native configs.
Configuration
In both Apache and LSWS-native configs, setting up HSTS is just a matter of adding a header.
Using Apache Configs, Such as cPanel and Plesk
If LSWS is using Apache configs, such as in a cPanel or Plesk environment, setting up HSTS is as simple as adding a header directive to your server or .htaccess configs. If you would like to enable it globally instead of on any particular virtual host, you can add it to the server level configuration, for example for cPanel, add it to pre_main_global configuration.
Header always set Strict-Transport-Security "max-age=31536000"
This header tells the client that interactions with the configured sites should always use HTTPS for one year (31536000 seconds).
Using LSWS-Native Configs
If you are using LSWS native configs, you will need to add a context with the new header. To do this, go into your virtual host's Context settings (WebAdmin > Virtual Hosts > your virtual host > Context > Add).
Since we only want to add an extra header, it is easiest to set up a static context. You can also add this header to any other context you already have set up.
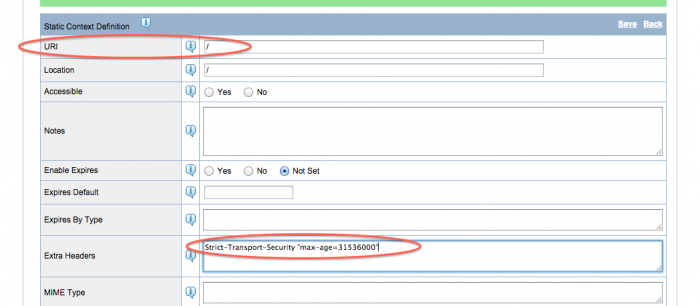
I want all pages for this virtual host to use HSTS, so I set the context URI to /. I then add the HSTS header into the Extra Headers setting: Strict-Transport-Security “max-age=31536000”. This header tells the client that interactions with the configured sites should always use HTTPS for one year (31536000 seconds).
When you're done, click Save, then perform a graceful restart to apply the changes.
Checking HSTS
Once the HSTS header has been added, you should be able to see Strict-Transport-Security: max-age=31536000 when viewing response headers. Running a curl -i script directed to one of the configured pages will show you the headers in addition to the site content.